Телеграм канал «ShitCoin 100X Shilling»

телеграм-каналов

рекламных размещений, по приросту подписчиков,
ER, количеству просмотров на пост и другим метрикам

и креативы
а какие хуже, даже если их давно удалили

на канале, а какая зайдет на ура

⚡️ Currently in the Community Sale stage at just $0.031 per QELT plus bonuses up to +45%! Don't miss out before it's listing.
⚡️ Total supply of 10 billion tokens, with 50% allocated to the community & airdrops. No private VC rounds – everything's transparent and fair for the public.
⚡️ Use QELT for gas fees, asset verification, and conversion to QXMP (a real-asset-backed stablecoin). The ecosystem is already live with QELT Hub, DEX, bridge, and staking!
⚡️ From TGE to global adoption, including regulatory stablecoin integrations and institutional liquidity. Presale ends soon – countdown's at about 10 days!
⚡️ BitMart has announced they'll list QELT at TGE! That means easy access to global trading on a trusted exchange right after launch. This project is backed by $1.2 trillion in assets, ready to transform how we interact with RWAs.
🔗 Official Links:
🌐 https://www.qelt.ai
✖️ https://x.com/qeltblockchain
💼 https://www.linkedin.com/company/qeltblockchain
💭 $TAO has just broken out from a falling wedge pattern on the 4-hour timeframe – this pattern often marks the end of a correction phase and the beginning of an uptrend.
💱 68% of the supply is in staking pools.
🔗 Official Links:
🌐Website | 💰Docs | 📔Whitepaper | ⚡️Explorer | 🦎CoinGecko | 🪙CMC | ✖️X/Twitter | 🎮Discord | 🐙Github
The Bittensor network has hit a monumental milestone: Full on-chain governance is live, and the Opentensor Foundation has officially stepped back, marking the end of centralized oversight. This transition empowers the community to drive the future of decentralized AI! 🤖
Leadership Shift: CEO Jacob Steeves (aka Const) and COO Ala Shaabana (ShibShib) have stepped down from executive roles but remain active as core contributors and subnet builders, no special privileges, just pure participation.
Triumvirate Ratification System: A new governance model with validators, subnet owners, and a senate veto mechanism ensures balanced, censorship resistant decisions. Urgent fixes pass in hours, major changes take weeks.
Nominated Proof-of-Stake Nodes: Chain nodes are now fully decentralized, with direct funding from fees for infrastructure.
No Single Point of Failure: Bittensor ($TAO) operates as a self-sustaining ecosystem where miners build AI models, validators score them, and rewards flow transparently, all without a CEO or central entity.
Bittensor, the decentralized AI network incentivizing machine intelligence through $TAO, is now truly "headless" and unstoppable. This move eliminates key-person risks and accelerates innovation in open-source AI, with subnets competing in real-time for utility and rewards.
Huge props to the team for putting mission over ego, the future of co-owned intelligence is here!
🔗 Official Links:
🌐Website | 💰Docs | 📔Whitepaper | ⚡️Explorer | 🦎CoinGecko | 🪙CMC | ✖️X/Twitter | 🎮Discord | 🐙Github
Today, we're discussing exciting developments from Shido Network, a super-fast and scalable L1 blockchain based on Proof-of-Stake. Shido isn't just an ordinary blockchain – they are heavily focused on on-chain agentic economy, aka AI-based autonomous systems on the blockchain. Currently, Shido has a speed of 15,000 TPS, making them one of the fastest in the crypto world!
⚡️ Nova Upgrade: A Major Revolution in 2026
The Nova Upgrade is version 3 (V3) of Shido Network, planned for full release in 2026. This isn't a minor update, but a total transformation to make the network faster, more secure, and user-friendly.
📔 Launch Phases:
- Nova Testnet ✅
- Nova Mainnet: Live Q1 2026 ♻️
Key Features That Will Blow Your Mind:
- Instant transaction confirmations in just 400 milliseconds (less than 1 second)! TPS will increase to 30,000 TPS.
- Upgradable without disrupting the main network.
- Stronger protection against attacks, with optimized consensus and execution.
- State store migration to V3, more efficient processes, and pruning of old data to keep the network lightweight.
This will make Shido ready to compete with centralized infrastructure like cloud servers, but still decentralized and secure! ⚠️
📈 2026 Roadmap: Focus on Optimization
Shido is building an ecosystem where low latency, high throughput, and maximum composability are priorities. The goal? To allow developers to build applications without limits, especially in DeFi, NFTs, and on-chain AI. They allocate block space intelligently, enhance the core network, and create better value flows for all parties.
📌 Latest Collaborations and Integrations
🪙 CMC Integration: Shido's on-chain data is now directly connected, including tokens, DEX, and ecosystem. Transparency levels up, making it super easy to track assets!
🤝 Strategic Partners: Collaborations with RoundtableSpace, AMINA Bank Global, Sygnum, and Arab Bank CH – this shows Shido is serious about entering the real financial world and DeFi.
💰 Supporting Applications: Non-custodial wallet for buying, storing, sending, and swapping assets. There's also a cross-chain DEX, NFT Gallery, and fiat on/off ramps that make entering and exiting crypto easier.
The crypto market is volatile right now, but Shido keeps building!
➡️ Explore More: https://shido.io
#ShidoNetwork #CryptoUpdate #BSCNews #DeFi #Blockchain2026
You are about to unlock exclusive access in the revolutionary Canopy Network – the peer-to-peer launchpad for sovereign appchains that's redefining blockchain creation with limitless scaling, security, and autonomy!
The Canopy Pass is now redeemable on the rewards hub. Mint yours today and be among the first to enjoy premium benefits like early ecosystem access, airdrop eligibility, governance perks, and community-driven rewards. Built for builders and innovators, Canopy empowers teams to launch app-specific chains that evolve from shared security to full independence – no compromises on speed (10,000+ TPS), customization, or sovereignty.
Powered by a recursive architecture and progressive autonomy model, Canopy makes blockchain deployment as simple as spinning up an app, with built-in atomic swaps and mesh security. Backed by strong funding and a growing community (20K+ on X), this is your gateway to the next era of Web3 innovation!
Don't miss out – claim now and shape the future!
👉 https://rewards.canopynetwork.org
#CanopyNetwork #CanopyPass #Appchains #Web3 #Blockchain #CryptoCommunity #DeFi #Layer1 #CryptoLaunch
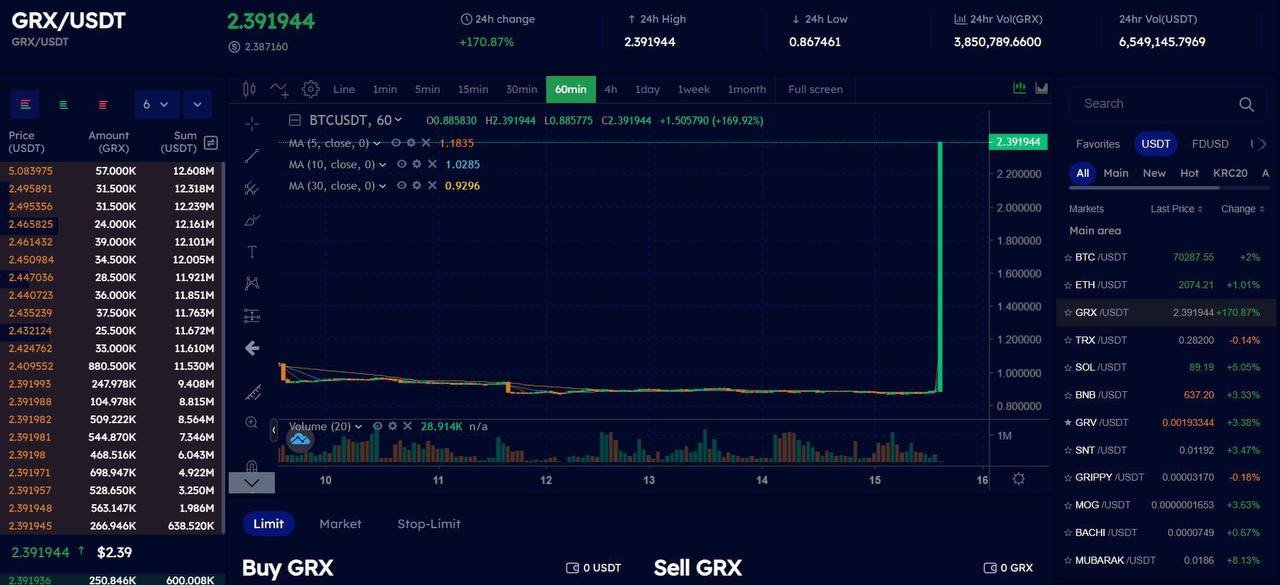
$GRX is one of the most interesting “CEX-backed L1” plays I’ve seen. The combination of a live exchange driving volume + a high-performance EVM chain + near-full circulation makes it stand out from typical new chains.
💱 EVM Compatible
🏦 Proof-of-Stake (DPoS)
🪧 20,000+ TPS with sub-second finality
🔓 Military-grade encryption + global node distribution (6 continents, 500+ validators)
⛏ Full EVM tools, APIs, SDKs, smart contracts — Ethereum dApps can migrate easily
📈 Tokenomics & Market Snapshot:
- Price: $2.97
- Market Cap: $28.35M
- FDV: $29.68M
- Circulating Supply: 9.55M / 10M max
- 24h Volume: $12.24M
- 24h Change: +237.9%
- 7d Change: +186.9%
- TVL: $1.3M
- Wallets: 1,217 (still very early)
- Blocks: 6.22M | Avg block time: 3.0s | Total tx: 203k
The chart is classic “post-ATL rocket”: huge rebound in 24–48 hours, strong volume, and community calling for more CEX listings (MEXC already being tagged).
✅ Important Links:
Website | Whitepaper | CoinGecko | Explorer | X/Twitter | Instagram
📌 The Zoth team is opening applications for their exclusive Ambassador Program: a small, elite cohort of passionate builders, creators, and advocates shaping the future of stablecoin-powered banking. High standards, massive impact – if you have the drive to redefine global on-chain finance, this is your call!
⚙️ Zoth is pioneering a next-gen neobank with stablecoin infrastructure, trust-first tools, and seamless payment rails. Open to content creators, devs, community mods, event hosts, and more – no Web3 experience needed, just commitment and passion.
Perks for ambassadors:
🔹 Experience in stablecoins, neobanking, and on-chain
🔹 Global networking with founders, devs, and leaders
🔹 Performance-based rewards tied to your impact
🔹 Exclusive early access to products, and events
🔹 Visibility on Zoth's channels + merch
🔹 Potential for full-time roles or partnerships
📝 Apply now: https://zoth.io/ambassador
#Zoth #ZothAmbassador #Stablecoins #Neobank #DeFi #Web3 #CryptoCommunity #BSCNews